Alert Archives
Suspicious Mobile Banking Alert Scam
Date: 19 November 2021
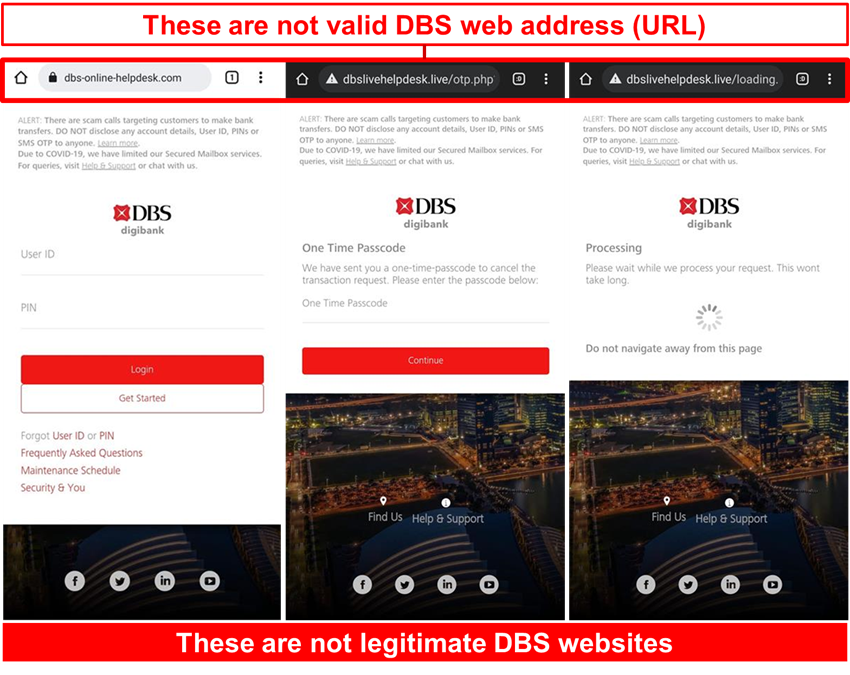
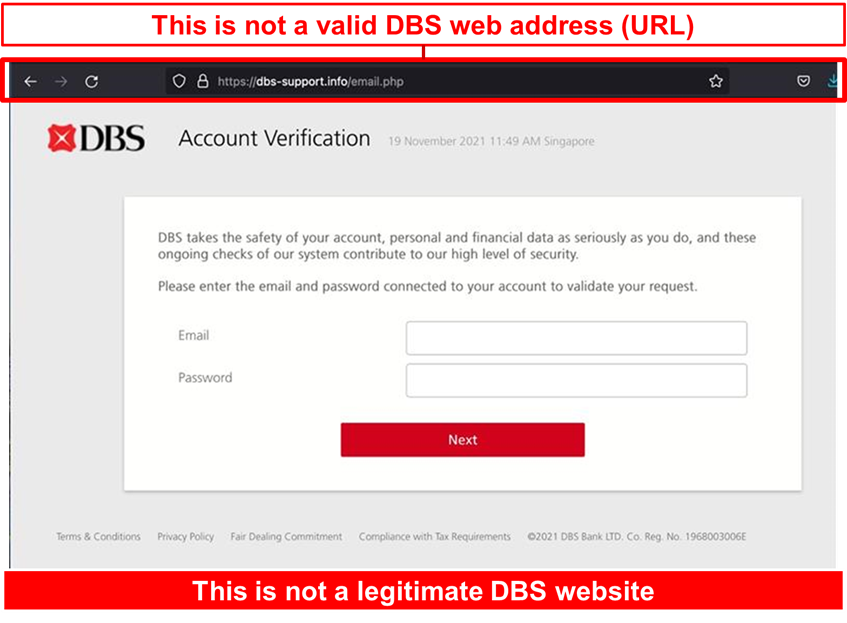
Description: Scammers are actively targeting DBS customers using the suspicious mobile banking alert scams. Targeted members of public are warned of unauthorized registration of the mobile banking application on a new mobile device and are asked to login to a phishing website to verify their details.
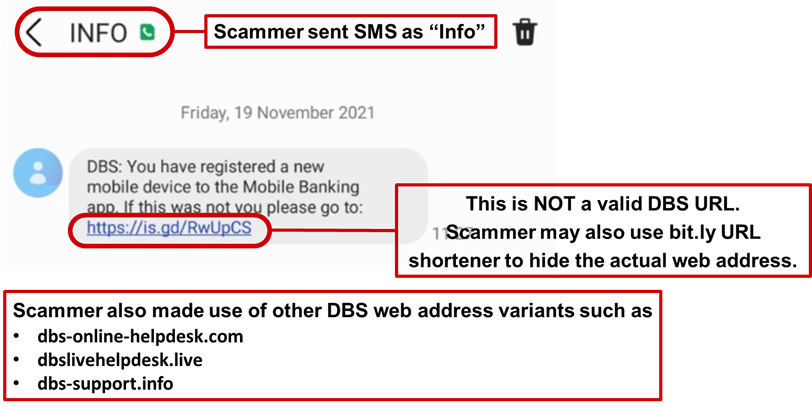
Users attempting to login to the fraudulent phishing site will be led through the following sequence of events:
- Victim will be directed to a phishing site to enter their online banking credentials i.e., User ID, Password and authorise access using the One Time Pin.
- Victim will be redirected to a page to provide their email address and password.
- Victim who provided the information will be informed that they have been successfully verified before being redirected to DBS Internet Banking page.
The scammer will exploit the stolen information to take over the victim’s Internet Banking account or make unauthorized fund transfer from the victim’s bank account.
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official website or use DBS’s official mobile applications to conduct any DBS bank-related requests. Go directly to https://www.dbs.com to ensure that you are on our website.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications. Do not give your credit card details out to unknown websites.
- DBS will never ask you for your credit card details, CVV or SMS OTP to verify or unlock your account.
- Do not click on any URL links or call numbers provided in unsolicited email messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your card numbers or OTPs to unverified sources. Bank staff and government officials will never request your card details or OTPs through SMS, voice calls, or unofficial websites.
Scamshield Feature - For Singaporean customers
ScamShield is an initiative by the Singapore Police Force and the National Crime Prevention Council, and more information can be found at https://www.scamshield.org.sg/.

Block scam calls – ScamShield compares an incoming call against a list maintained by the Singapore Police Force to determine if the number has been used for illegal purposes and blocks it.
Filter scam SMSes – When you receive an SMS from an unknown contact, ScamShield will determine if the SMS is a scam using an on-device algorithm and filter the messages to a junk SMS folder. Scam SMSes will be sent to NCPC and SPF for collation. This keeps the app updated and will help protect others from such scam calls and messages.
Report scam messages – You can also report scam messages from other chat apps such as WhatsApp, Wechat, IMO, Viber, etc. You can forward the messages via ScamShield’s in-app reporting function.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Suspicious Login Alert Scam
Date: 16 November 2021
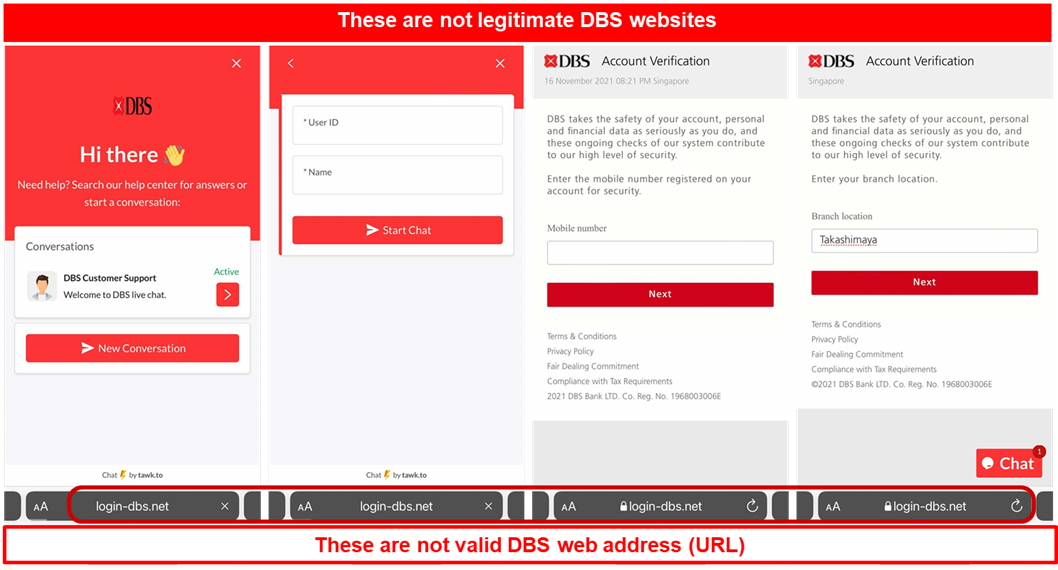
Description: Scammers are actively targeting DBS customers using suspicious login alert scams. Targeted members of the public are warned of an unauthorized login attempt to the account and are asked to login to a phishing website to verify their details.
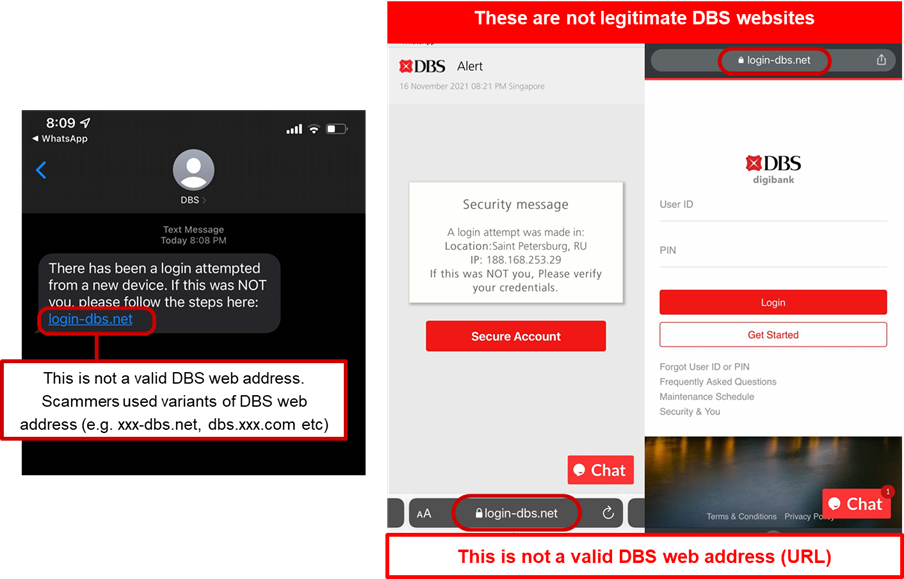
Users attempting to login to the fraudulent phishing site will be led through the following sequence of events:
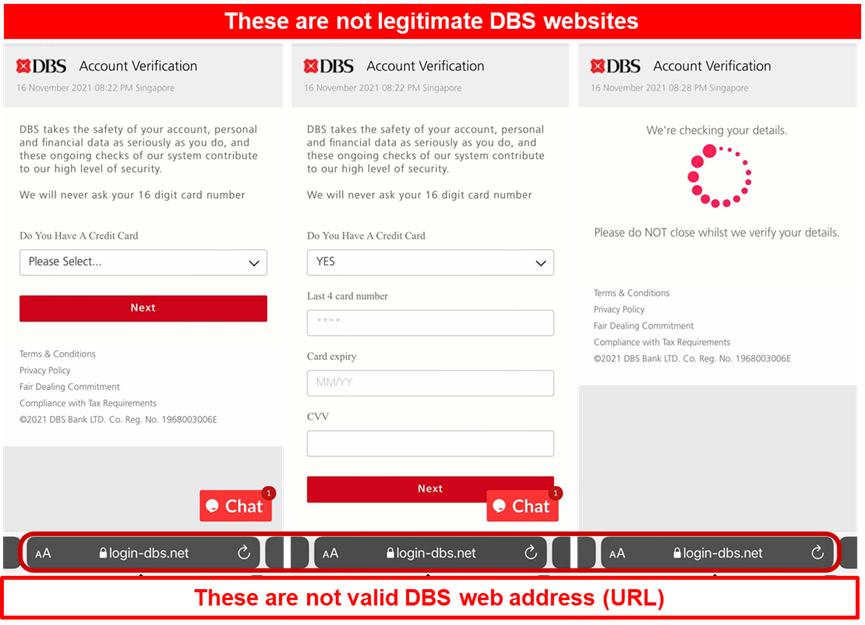
- Victim will be directed to a customer support live chat page, which requires the victim to provide information such as Bank account ID, name, mobile number and bank branch information.
- Victim will be redirected to a page and required to provide their credit card details.
- Victim who provided the information will be informed that they have been successfully verified before being redirected to the DBS Internet Banking page.
The scammer will exploit the stolen information and credit card details to take over the victim’s Internet Banking account or charge fraudulent card transactions to the customers’ credit and debit card or take over their Internet Banking account.
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official website or use DBS’s official mobile applications to conduct any DBS bank-related requests. Go directly to https://www.dbs.com to ensure that you are on our website.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications. Do not give your credit card details out to unknown websites.
- DBS will never ask you for your credit card details, CVV or SMS OTP to verify or unlock your account.
- Do not click on any URL links or call numbers provided in unsolicited email messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your card numbers or OTPs to unverified sources. Bank staff and government officials will never request your card details or OTPs through SMS, voice calls, or unofficial websites.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Suspicious Login Alert Scam
Date: 05 November 2021
Description: Scammers are actively targeting DBS customers with the Bicentennial Commemorative Note scam. Targeted members of the public will receive an SMS from a sender “Notice” to inform them that they are to receive a Bicentennial Commemorative Note worth $20 for free. These individuals will be directed to click on the phishing URL, which uses a variant of www[.]dbs-xxx.com, and requested to login to their DBS Internet Banking accounts.
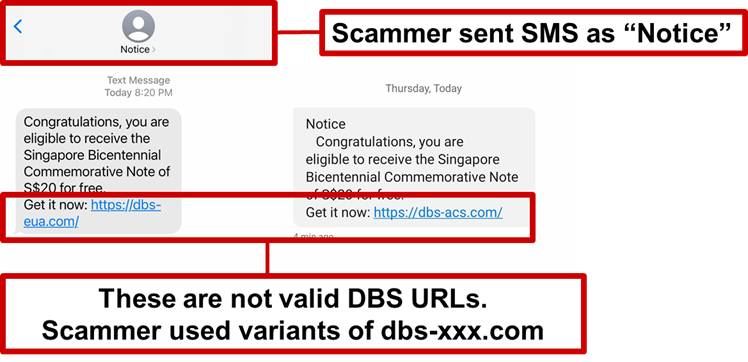
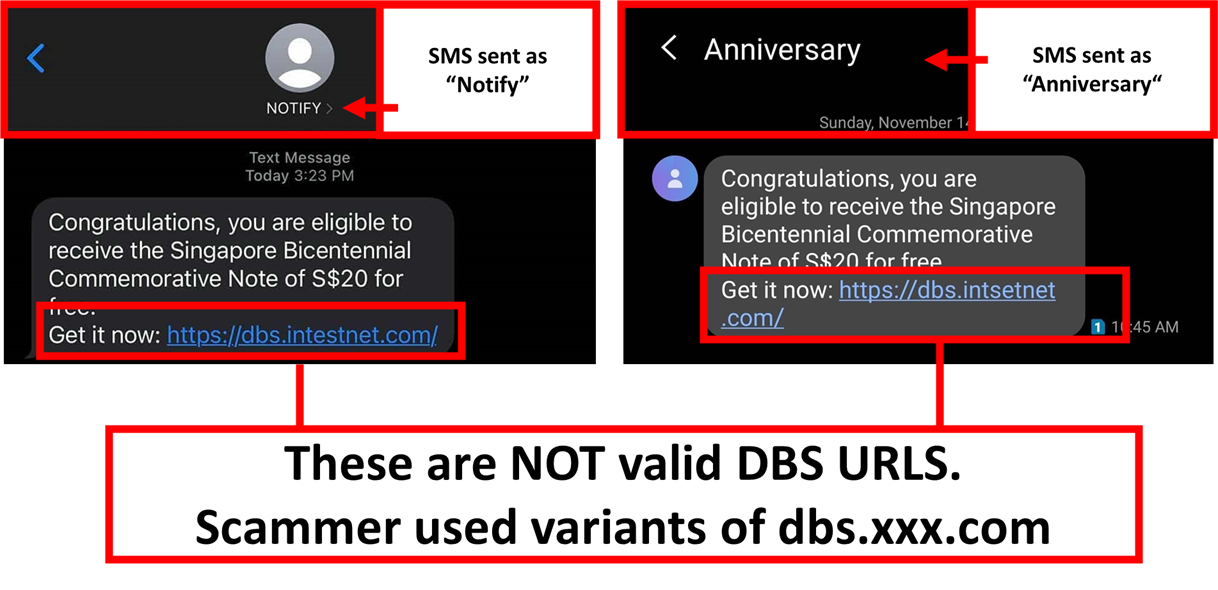
Once logged into the fraudulent phishing site, the scammer will access the victims’ internet banking account and conduct unauthorized transactions from the victims’ accounts.
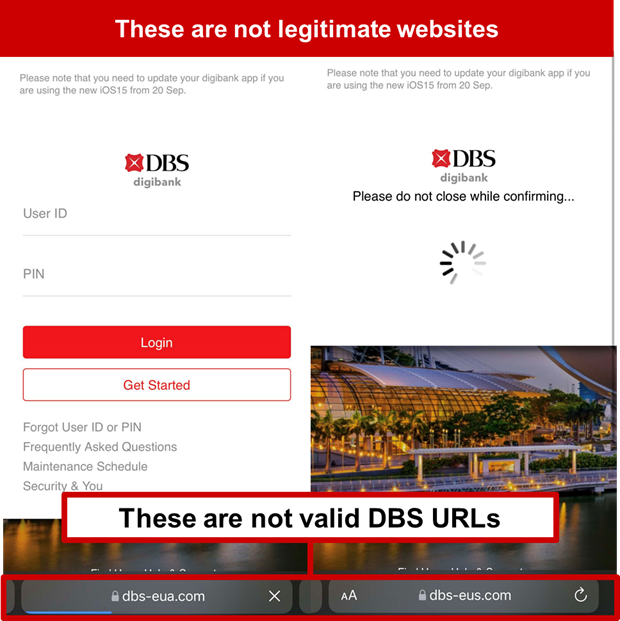
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official website or use DBS’s official mobile applications to conduct any DBS bank-related requests. Go directly to https://www.dbs.com to ensure that you are on our website.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications. Do not give your credit card details out to unknown websites.
- DBS will never ask you for your credit card details, CVV or SMS OTP to verify or unlock your account.
- Do not click on any URL links or call numbers provided in unsolicited email messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your card numbers or OTPs to unverified sources. Bank staff and government officials will never request your card details or OTPs through SMS, voice calls, or unofficial websites.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Suspicious Login Alert Scam
Date: 23 October 2021
Description: Scammers are actively targeting DBS customers using suspicious login alert scams. Targeted members of the public are warned of an unauthorized login attempt to the account and are asked to login to a phishing website to verify their details. Once logged into the fraudulent phishing site, the victims will be led through the following sequence of events:
- Victim will be directed to a page that requires the victim to provide personal information such as name, date of birth, phone number, email address, home address, mother’s maiden name, etc.
- Victim will be redirected to a page and required to provide their credit card details.
- Victim who provided the information will be informed that they have been successfully verified before being redirected to the DBS Internet Banking page.
The scammer will exploit the stolen Internet Banking credentials, personal information and credit card details to take over the victim’s Internet Banking account or charge fraudulent card transactions to the customers’ credit and debit card.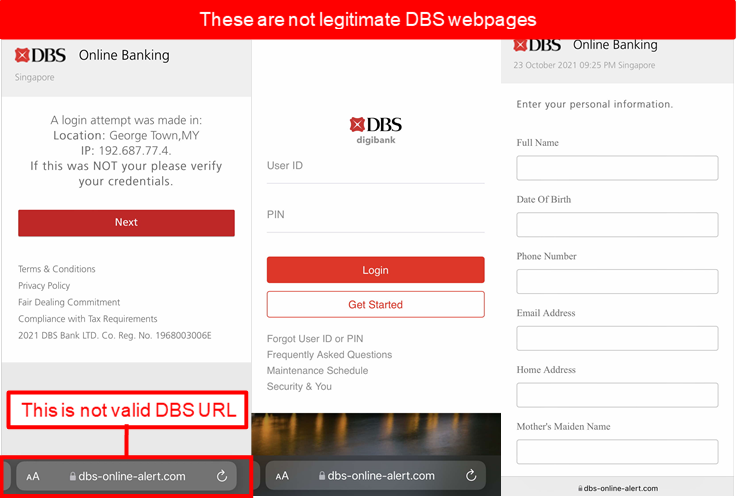
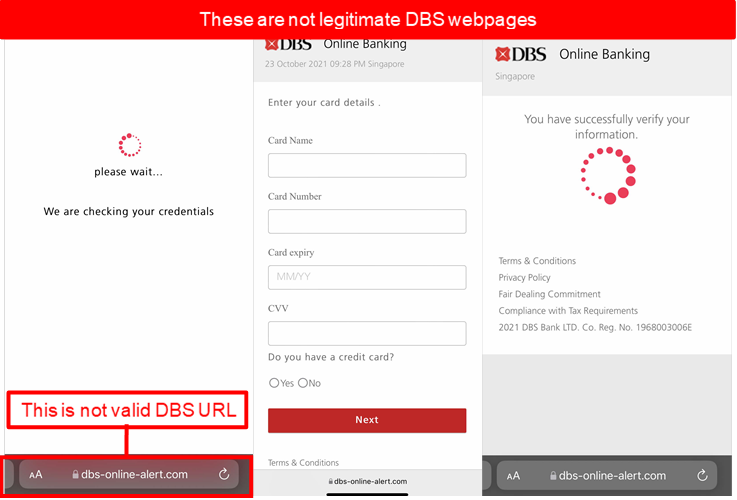
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official website or use DBS’s official mobile applications to conduct any DBS bank-related requests. Go directly to https://www.dbs.com to ensure that you are on our website.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications. Do not give your credit card details out to unknown websites.
- DBS will never ask you for your credit card details, CVV or SMS OTP to verify or unlock your account.
- Do not click on any URL links or call numbers provided in unsolicited email messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your card numbers or OTPs to unverified sources. Bank staff and government officials will never request your card details or OTPs through SMS, voice calls, or unofficial websites.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
DBS Promotion Scam and Phishing Alert
Date: 24 September 2021
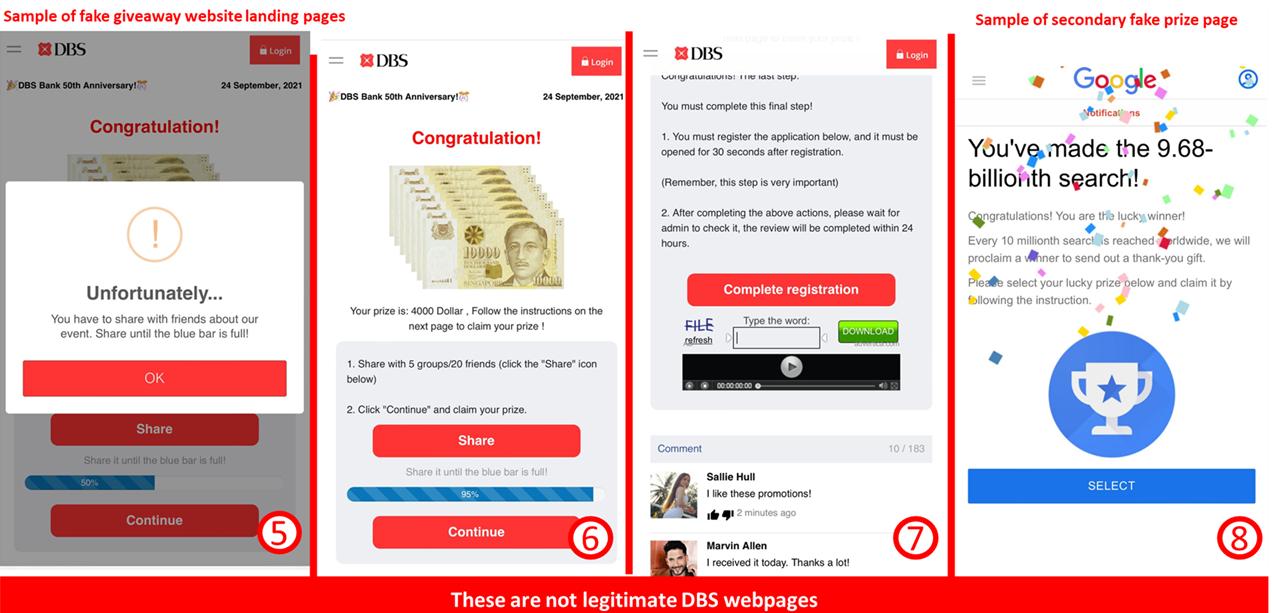
Description: Scammers are actively targeting the public with fictitious DBS 50th Anniversary Giveaway promotions. Participants are enticed to share the scams with their contacts via WhatsApp to claim the prize money of SG$4000 or the equivalent in local currency. Victims who attempted to claim the prize money after sharing the scam with their contacts are redirected to another fraudulent site and will be led through the following sequence of events:
- The page will request the user to fill in sensitive information such as their home address and credit card details.
- A prompt for the user to forward the link through a messaging application such as WhatsApp.
- A secondary scam prize opportunity asking for your credit card information or offering items at prices well below market rate.
Victims of this scam may receive fraudulent charges on their cards and put themselves and their contacts at risk of being targeted by future scams.
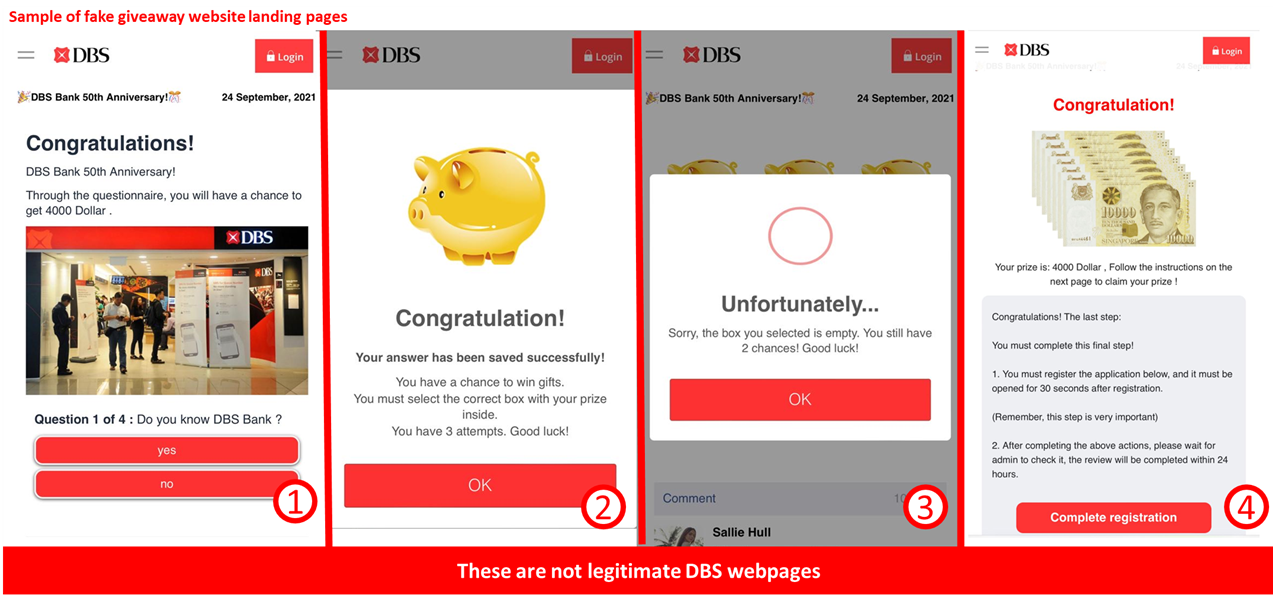
Customers are advised to be mindful of such scams..
Always ensure you are on DBS’s official website or use DBS’s official mobile applications. Go directly to https://www.dbs.com to ensure that you are on our website to verify if there are any official giveaways or promotions.
Remember: Do not give your credit card details out to unknown websites.
- Do not click on any URL links in unsolicited email messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your card numbers or OTPs to unverified sources.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Government Official Impersonation
Date: 16 September 2021
Who might be at risk?
DBS and POSB customers
Description: Scammers are actively impersonating government officials such as the Ministry of Health, Chinese authorities, or other government officials to defraud our customers. They may use baits such as:
- Contact Tracing,
- Covid-19 Test Updates,
- Money laundering and tax evasion offences,
- An individual’s phone number being used to spread falsehoods or scams relating to Covid-19 in China.
These scammers may contact individuals through messaging programs such as WhatsApp or voice calls.
If an individual falls victim to these claims, the scammer may ask for the following information or request the victim conduct the following actions:
- Internet Banking credentials,
- OTP or Digital Token approval,
- Performing fund transfer(s) to another account.
Similar scams in the past have impersonated the Singaporean Ministry of Health, Singapore Police Force, or DBS Staff.
Customers are advised to be mindful of such calls.
- Government officials will never ask for your financial details or fund transfers over the calls. Always check for the authorities' contact information on the official websites and verify the calls via the government agency’s hotline if you receive such calls. Do not proceed further if the caller asks for your information, banking credentials, or conducts suspicious or unfamiliar actions or transactions.
- Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites or mobile applications. Do not give your credit card details out to unknown websites.
Call us immediately at the hotlines below if you receive or suspect you’re a victim of fraud.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Fake Bank Website Alert
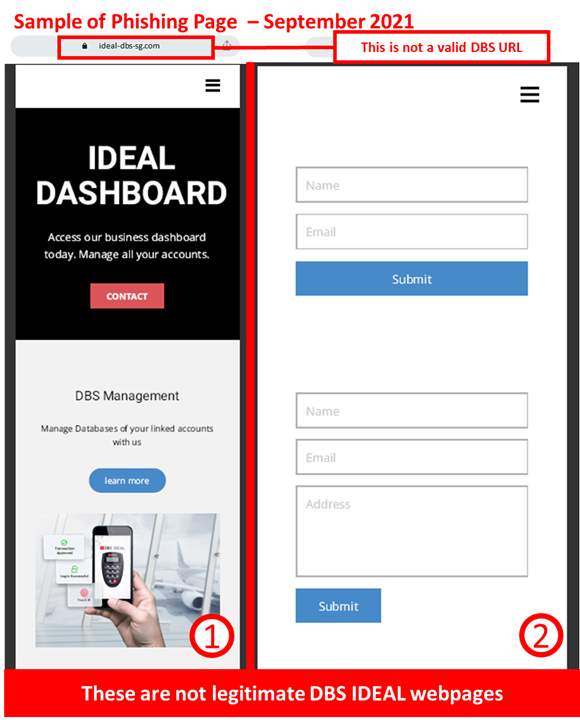
Date: 15 September 2021
Description: Scammers have created fake DBS IDEAL web pages to trick users into providing their contact details to non-DBS parties. This website asks a user to provide a name, email, and company address.
If an individual provides this information, they may be subject to an impersonation scam by fraudsters purporting to be DBS staff through email, voice, or messaging applications.
Customers are advised to be mindful of such calls.
Do not give out your IDEAL or DBS-related logins, OTPs, or Digital Token Approvals, to other individuals, non-DBS websites, or mobile applications. Neither DBS Staff nor government officials will ask for your logins or OTPs through calls, SMS, emails, or unofficial websites.
Customers are reminded to ensure they are on DBS’s official web pages or use DBS’s official mobile applications to conduct any DBS Bank or IDEAL requests. Go directly to https://www.dbs.com to ensure that you are on our website and do not conduct any DBS-related logins on other websites.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 06 August 2021
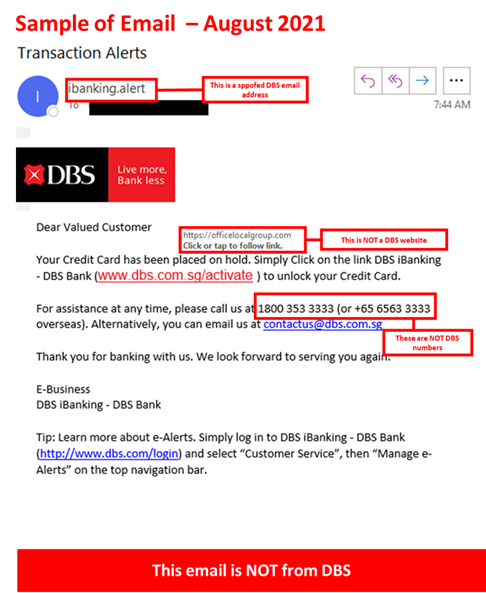
Description: Scammers are making use of fake DBS transaction alerts via phishing emails and phishing sites to steal DBS card details and charge fraudulent transactions on the victims’ credit and debit cards.
If a customer falls victim to this scam, the scammer will exploit the stolen card information and charge fraudulent card-not-present transactions to the customer’s credit, debit, or ATM card. Customers who respond to the scam will be directed to the following sequence of events:
- An email claiming the customer’s credit card is on hold and needs to be unlocked through a non-DBS website.
- A website asking for the user to provide their credit card information, PIN, and CVV.
- A secondary screen asking for the customer’s SMS OTP.
- Should a customer complete these requests, they will be redirected to DBS’s legitimate main page.
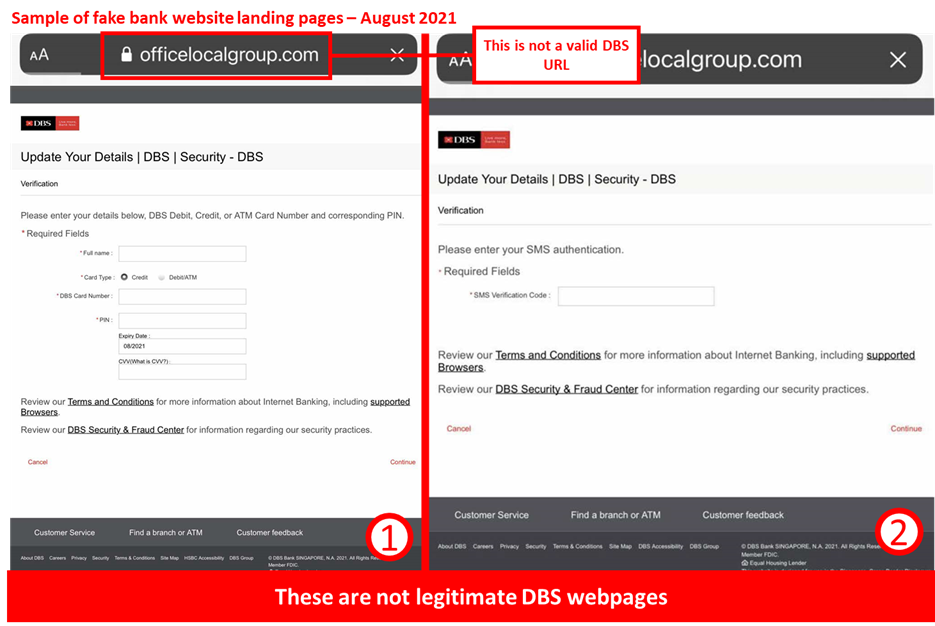
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official website or use DBS’s official mobile applications to conduct any DBS bank-related requests. Go directly to https://www.dbs.com to ensure that you are on our website.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications. Do not give your credit card details out to unknown websites.
- DBS will never ask you for your credit card details, CVV or SMS OTP to verify or unlock your account.
- Do not click on any URL links or call numbers provided in unsolicited email messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your card numbers or OTPs to unverified sources. Bank staff and government officials will never request your card details or OTPs through SMS, voice calls, or unofficial websites.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 14 July 2021
Description: Scammers are using fake DBS Internet Banking phishing sites to steal customers’ DBS credentials and OTPs in order to gain access to their PayLah! accounts.
If a customer falls victim to this scam, the scammer will gain full control of the customer’s DBS PayLah! account to conduct unwanted funds transfers or lock the customer out of their account by setting the scammer’s phone as the approved device.
Customers are reminded not to accept any unauthorized requests or provide OTP or Digital Token approvals unless they initiate the request themselves.
Should a customer fall victim to this scam, they will see the following sequence of events:
- The fraudulent website will display a prompt stating “Please note that your holding funds will be credited into the account you are about to sign in. Click okay to continue.”,
- The customer will be redirected to a page requesting for the customer’s mobile number followed by asking for the customer to login to their DBS account,
- The customer will receive an OTP at their registered email address and will be asked to input this OTP to the fraudulent site,
- If a customer completes this step, the fraudulent website will ask for the OTP sent to the customer’s mobile phone and the customer’s PayLah! password.
- A final prompt will be seen stating “A problem persist, please try login in again.”
Once this sequence is completed, the scammer will have the necessary information to set their device as the approved PayLah! device, giving them full access to the customer’s PayLah! funds and preventing the customer from accessing their PayLah! account.
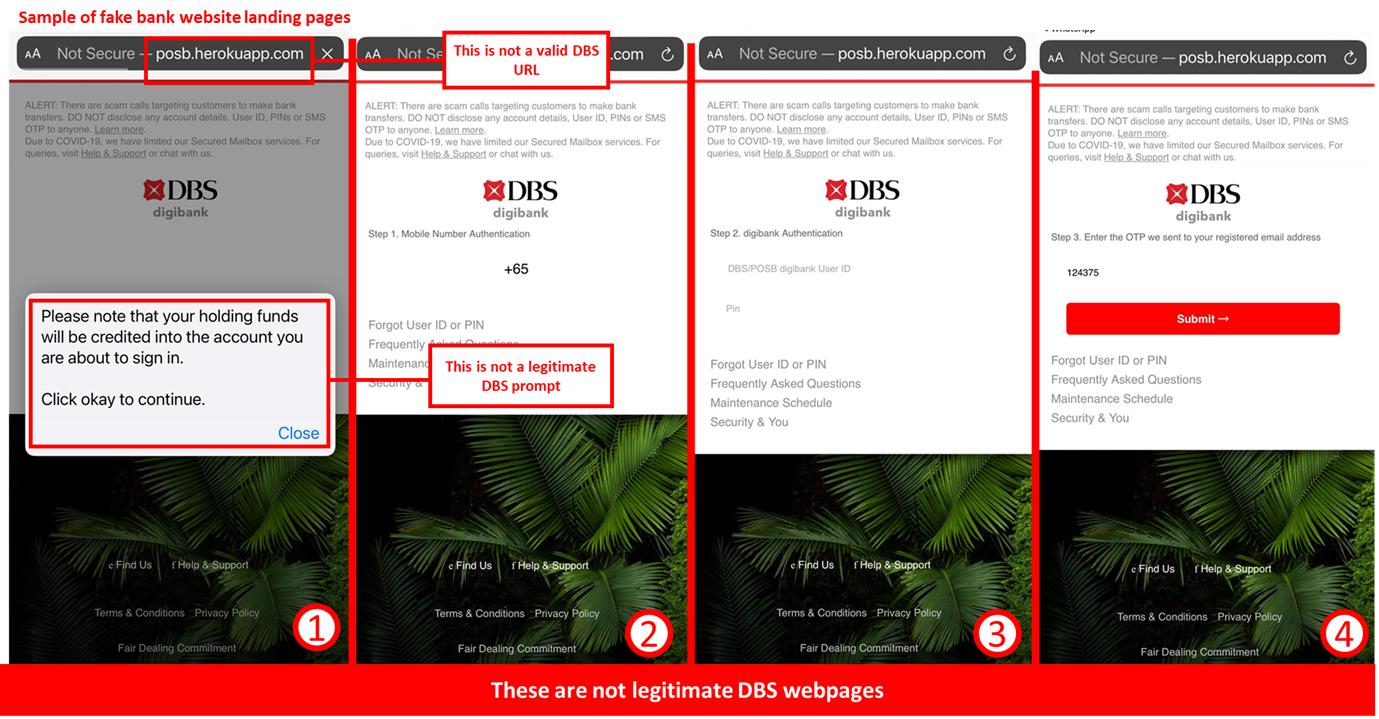
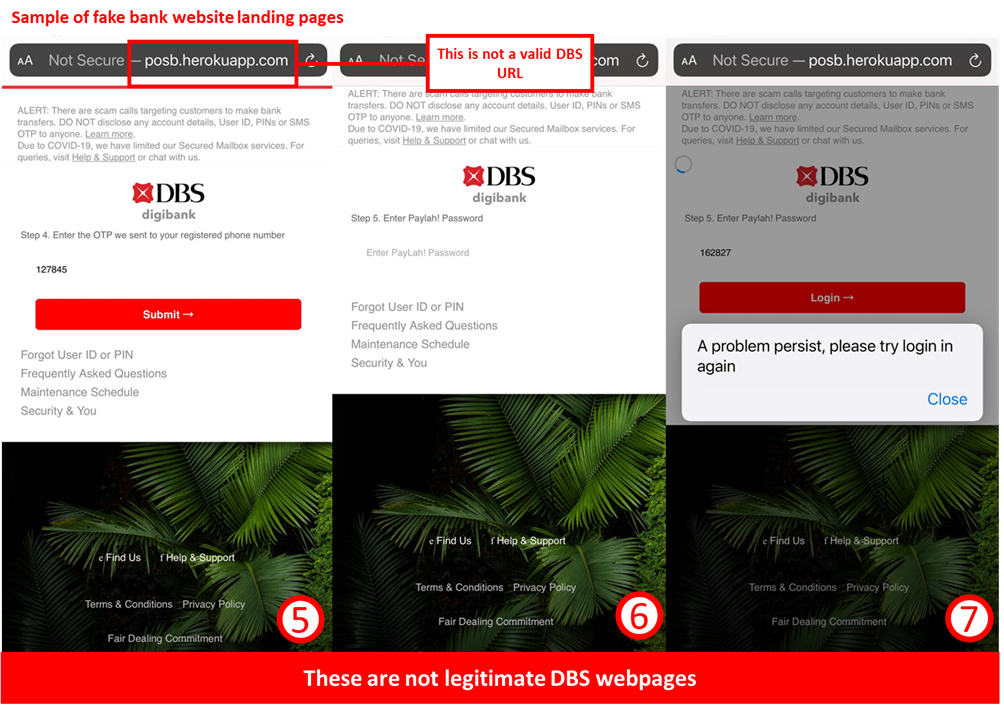
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official web pages or use DBS’s official mobile applications to conduct any DBS Bank or PayLah! requests. Go directly to https://www.dbs.com to ensure that you are on our website and do not conduct any DBS-related logins on other websites.
Remember: Do not give out your Internet Banking or PayLah! credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications.
- DBS will never ask you for your PayLah! password or OTP outside of your PayLah! app. Avoid inputting your passwords or OTPs in non-DBS URLs or applications.
- Do not click on any URL links or call numbers provided in unsolicited text messages.
- Always verify the authenticity of the message with the official websites or sources.
- Never disclose your Internet Banking or other sensitive details or OTPs to unverified sources. Bank staff and government officials will never request for your login details or OTPs through SMS, voice calls, or unofficial websites.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 05 July 2021
Description: Scammers are setting up DBS Internet Banking phishing sites to steal usernames, passwords and one-time pins from our customers. If customers fall victim and log into the phishing sites, the scammer will gain access to their DBS Internet Banking account, conduct unwanted funds transfers, or lock the customer out of their account by provisioning the customer’s DBS or PayLah! account on the scammer’s phone.
Customers are also advised not to accept any unauthorised requests or provide OTP approvals coming to their PayLah! or Internet banking unless they initiated the request themselves.
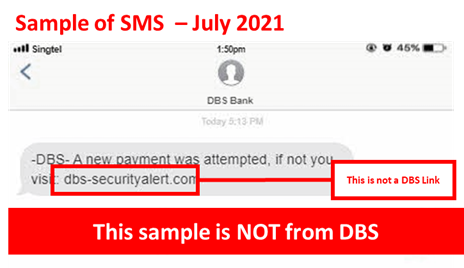
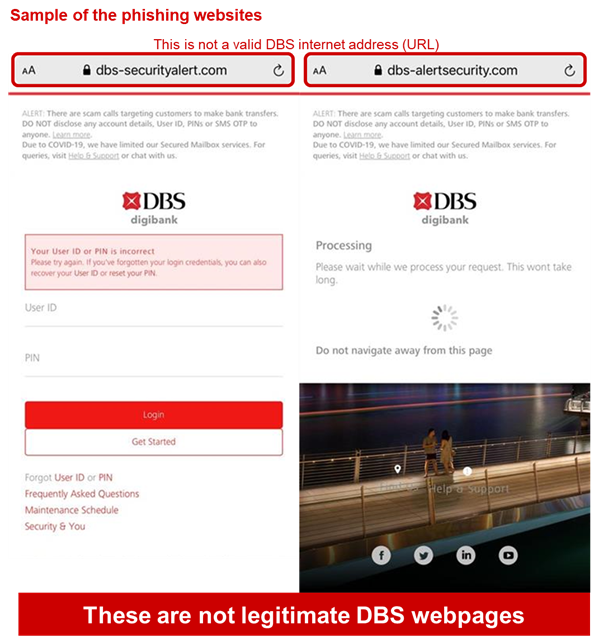
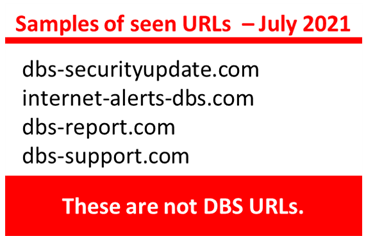
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official web pages or use DBS’s official mobile applications to conduct any DBS Bank or PayLah! requests. Go directly to https://www.dbs.com to ensure that you are on our website and do not conduct any DBS-related logins on other websites.
DBS will never ask you for your PayLah! password or OTP outside of your PayLah! app. Avoid inputting your passwords or OTPs to non-DBS URLs or applications.
Remember: Do not give out your Internet Banking or PayLah! credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites or mobile applications.
Avoid clicking on any URLs in unsolicited emails or smses, and always check with the source to ensure the message is legitimate.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Scam Alert
Date: 10 June 2021
Description: Scammers are using fake job applications to trick customers into making fund transfers. These fictitious job applications may be posted on various social media and job websites or disseminated through messaging platforms, SMS, or email.
These messages often promise high daily salaries, easy working conditions, or high commission rates to entice individuals into contacting the scammer. Such SMS messages may spoof a company's SMS shortcode (display name) and may be included in existing SMS threads with legitimate notifications.
If a customer responds to the scam, they may experience the following sequence of events:
- The customer will be directed to a fake shopping platform to buy an item by transferring payment to the scammer’s bank account.
- To build trust, the scammer will immediately make payments for the items in full with a 10% commission to the victim for the first few transactions.
- After the initial transactions, the victim will be asked to purchase and transfer payments for more items; however, no additional payment or commission will be made to the victim.
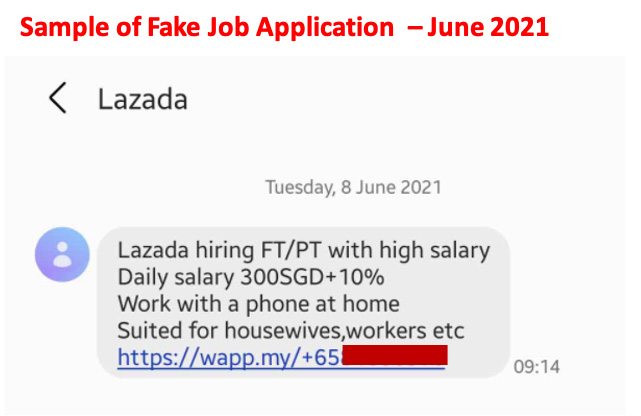
Customers are advised to be mindful of such scams.
Be cautious of and avoid job offers that promise a high return for minimal effort or ask for payment before you start work.
Remember: Do not give out your Internet Banking or PayLah! credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications.
Visit ScamAlert.sg for more information on Job Scams: https://www.scamalert.sg/scam-details/job-scam
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 31 May 2021
Description: Scammers are impersonating DBS Bank to conduct DBS Paylah!-focused phishing. This scheme attempts to steal DBS credentials and trick customers into sending funds or giving access to their PayLah! accounts.
If a customer falls victim to this scam, the scammer may gain access to their DBS Bank and PayLah! accounts, conduct unwanted funds transfers, and lock the customer out of their account by provisioning the customer’s DBS or PayLah! account on the scammer’s phone.
Customers are also advised not to accept any unauthorised requests or provide OTP approvals coming to their PayLah! or Internet banking unless they initiated the request themselves.
Should a customer fall victim to this scam, they will see the below sequence of events.
- A screen asking for the customer’s mobile number authentication will pop up
- A prompt stating “Please note that you holding funds will be credited into the account you are about to sign in. Click okay to continue.”,
- The customer will be asked to log into their DBS account,
- They will be asked to provide their SMS OTP or DigiToken approval,
- The customer will finally be asked for their PayLah! password.
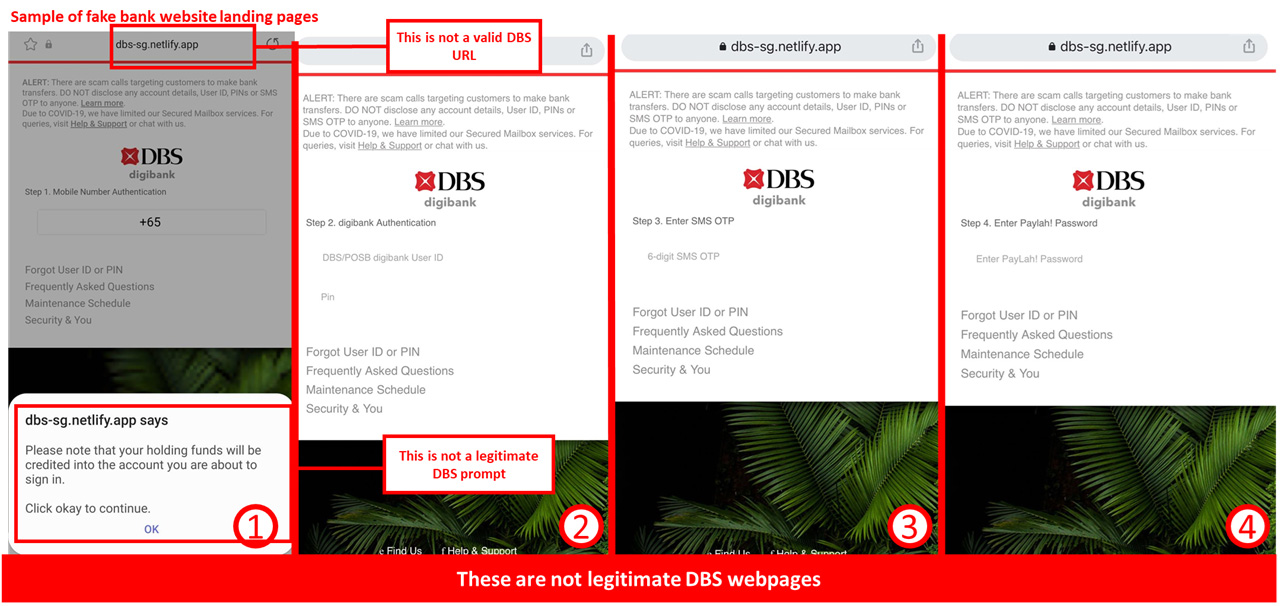
Customers are advised to be mindful of such scams.
Customers are reminded to ensure they are on DBS’s official web pages or use DBS’s official mobile applications to conduct any DBS Bank or PayLah! requests. Go directly to https://www.dbs.com to ensure that you are on our website and do not conduct any DBS-related logins on other websites.
DBS will never ask you for your PayLah! password or OTP outside of your PayLah! app. Avoid inputting your passwords or OTPs to non-DBS URLs or applications.
Remember: Do not give out your Internet Banking or PayLah! credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals, non-DBS websites, or mobile applications.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Malware Alert
Date: 20 May 2021
Description: Scammers are impersonating DBS Bank in order to phish unsuspecting users into both opening a malicious file and provide sensitive information, and may result in financial loss, their devices being infected, and even theft of their sensitive information. Emails sent by the scammer may masquerade as a PayLah! Alert or an invoice payment from DBS Bank and may contain a malicious attachment or link to a malicious file.
If you open the malicious file or click on the links, it may trigger a malware infection of your computer or mobile phone. The malware may steal your passwords and personal information or encrypt your files for a ransom (i.e. ransomware). Alternatively, the malware may also ask you to log in or provide other confidential information under the guise of opening the file.
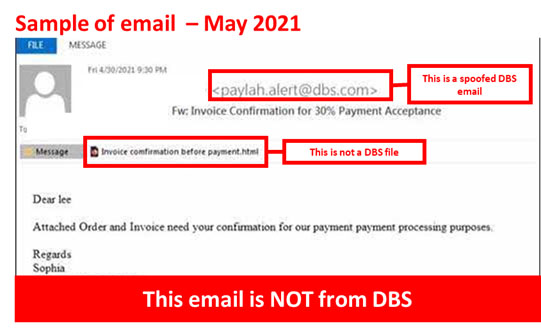
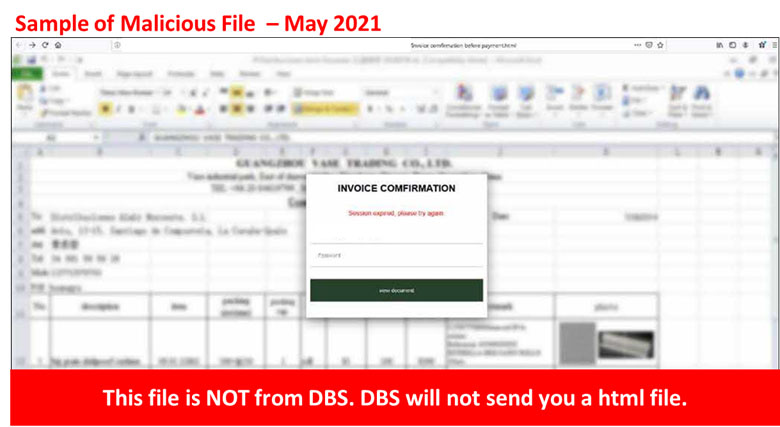
Customers are advised to be mindful of such scams.
If you receive a similar message or are contacted through social media by individuals claiming to be associated with DBS, stop, check, and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals.
Always ensure that you are on DBS’s official web pages by typing DBS’s website directly into the address bar on the browser or use our official mobile applications.
If available, use an antivirus to keep your devices secure. Learn more about keeping yourself secure by clicking on the Security Tips link on the right.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Advance Fee Fraud Alert
Date: 27 April 2021
Description: Scammers are impersonating DBS Bank in order to conduct advance fee fraud scams. An advance fee fraud scam uses an attractive reward as bait and requires an individual to pay a fee upfront in order to obtain the item. Commonly used rewards are services, stocks, contracts, or large amounts of money.
If a user accesses this fake website, they may be asked to log in, provide other sensitive information under the guise of opening a DBS account, or to provide payment to the scammer. Users who fall victim to this scam may be subject to identity theft, future phishing attempts, and monetary loss.
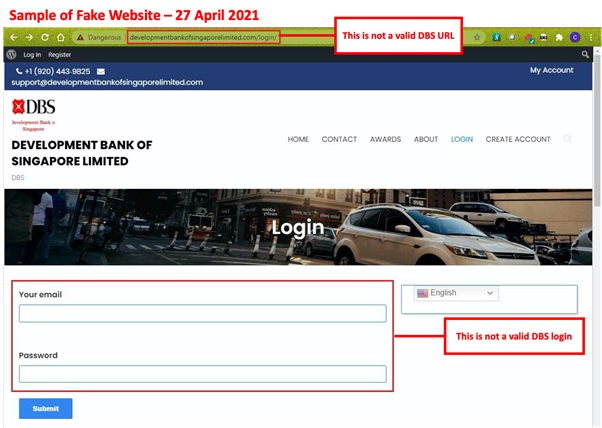
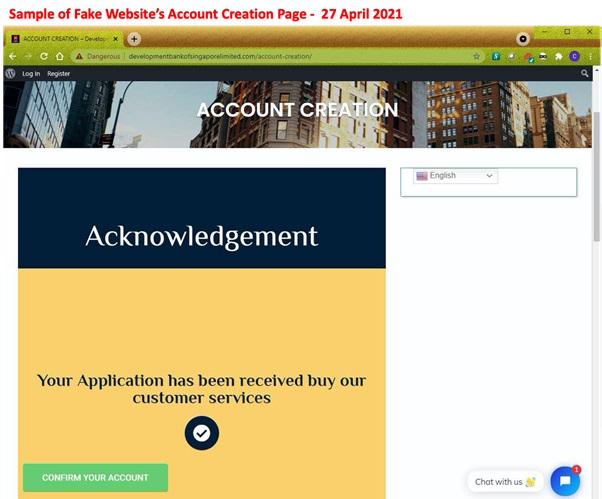
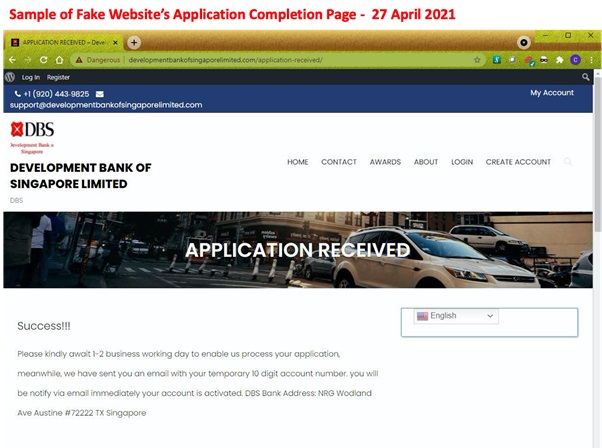
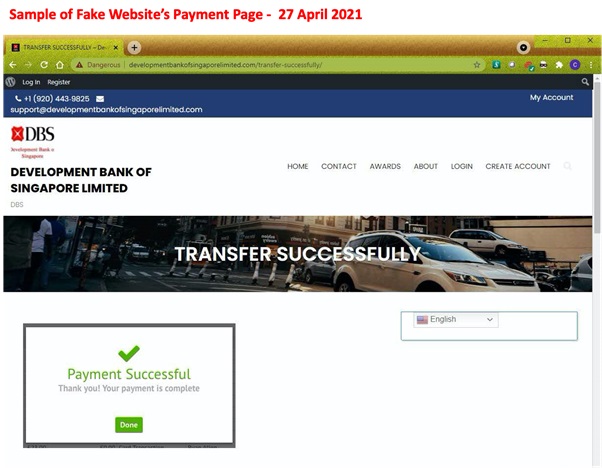
Customers are advised to be mindful of such scams.
Remember:Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals.
Always ensure that you are on DBS’s official web pages by typing DBS’s website directly into the address bar on the browser or use our official mobile applications.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Social Media Phishing Alert
Date: 14 April 2021
Description: Scammers are actively conducting social engineering scams in Singapore to gain access to customers’s bank accounts and conduct fraudulent bank transfers.
Customers are advised not to accept any unauthorised requests or provide OTP approvals coming to their PayLah! or Internet banking unless they initiated the request themselves. Customers are reminded to always read the message explaining what the OTP is for before taking action or approving it.
These scams are conducted through the official delivery applications as well as through online sellers.
The scammer requests for the customer’s mobile number under the guise of initiating a PayLah! transfer.
Once the victim has provided their mobile number, they will receive another SMS from the scammer requesting for them to log into their PayLah! account and enter a One Time Password (OTP) to link their PayLah! account with the scammer’s Google Pay account.
After completing the steps instructed by the scammers, PayLah! account will be compromised and allow the scammer to make multiple unauthorized transactions.
Customers are advised to be mindful of such scams.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals.
DBS PayLah! users do not need to link their DBS PayLah! account to their Google Pay account to receive money. You will need to link accounts only when sending money from Google Pay.
Monitor services connected to PayLah! By going to “Manage Link Service” and disable any services you no longer use with PayLah!
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Social Media Phishing Alert
Date: 01 February 2021
Description: Scammers are actively targeting DBS customers by sending fraudulent messages from compromised WhatsApp or other messaging applications accounts. These scammers exploited the compromised accounts to target the hacked user’s contacts and exploit the trust between the victims.
These messages may purport to be a part of an online shopping campaign such as Qoo10 and prompt the user to click on a link to a fake DBS login portal. Should a customer fall victim and click on the link, the phishing site will ask for the victim’s Internet Banking credentials, OTP or Digital Token approval to perform unauthorized fund transfers to another account.
A sample of the message is below:
“Qoo10 has a special campaign for the 10th year anniversary. I need only 5 votes. I will send you a message and you will receive a code via texst message can you send me that code?
Link: <Fake DBS website>.”
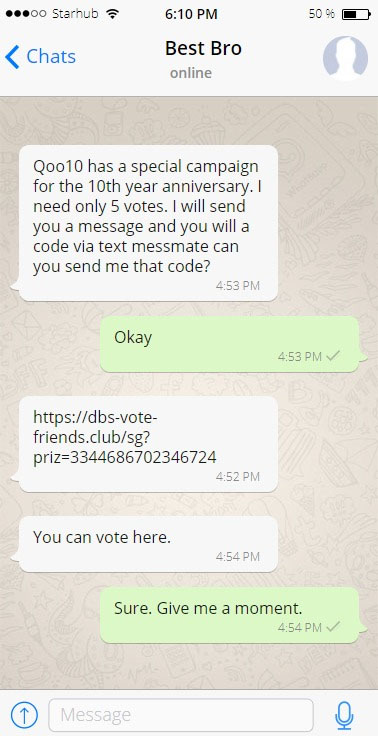
Customers are advised to be mindful of such requests on social media and go directly to our website or DBS-owned social media pages.
If you receive a similar message or are contacted through social media by individuals claiming to be associated with DBS, stop, check, and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals. Always go directly to our website to log into your iBanking account.
Singapore-based DBS and POSB customers using iPhone can also install and set up ScamShield® to block scam calls, filter scam SMSes, or report scam messages.
Scamshield Feature
ScamShield is an initiative by the Singapore Police Force and the National Crime Prevention Council, and more information can be found at https://www.scamshield.org.sg/.

Block scam calls – ScamShield compares an incoming call against a list maintained by the Singapore Police Force to determine if the number has been used for illegal purposes and blocks it.
Filter scam SMSes – When you receive an SMS from an unknown contact, ScamShield will determine if the SMS is a scam using an on-device algorithm and filter the messages to a junk SMS folder. Scam SMSes will be sent to NCPC and SPF for collation. This keeps the app updated and will help protect others from such scam calls and messages.
Report scam messages – You can also report scam messages from other chat apps such as WhatsApp, Wechat, IMO, Viber, etc. You can forward the messages via ScamShield’s in-app reporting function.
Call us immediately at the hotlines below or message our chatbot if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Email Alert
Date: 25 January 2021
Description: Scammers are exploiting DBS announcement of the replacement of the physical token with the digital internet/ mobile banking token in an attempt to defraud our customers.
The scammers are targeting DBS and POSB customers with phishing emails and calls on the pretext of assisting our customers to set up their digital token to prevent their accounts from being blocked.
Unsuspecting customers who fall victim to the scam are requested for sensitive information such as Digital Token approval or verification codes sent to the customer’s email or phone number. This information is used by the scammers to set up and link a digital token to the customers’ account to conduct unauthorized fund transfers and modifications while preventing the customer from accessing our internet and mobile banking services.
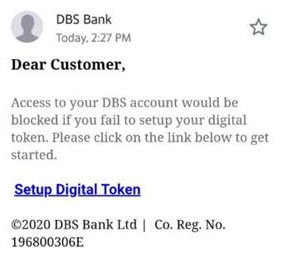
Customers are advised to be mindful of such emails and calls and to go directly to our website instead of clicking on links in such SMS.
If you receive a similar email or have been contacted by individuals claiming to be DBS staff, stop, check and exercise caution before you act. Singaporean customers are advised to pay attention to the ‘+’ on any calls they receive as they may not be a spoofed number.
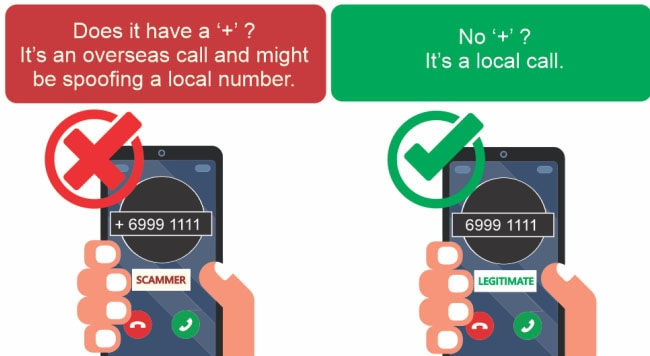
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals. DBS will never use voice or instant messaging apps like Whatsapp or Viber to contact you.
DBS and POSB customers using iPhone can also install and setup ScamShield® to block scam calls, filter scam SMSes or report scam messages.
FEATURE

Block scam calls – ScamShield compares an incoming call against a list maintained by the Singapore Police Force to determine if the number has been used for illegal purposes and blocks it.
Filter scam SMSes – When you receive an SMS from an unknown contact, ScamShield will determine if the SMS is a scam using an on-device algorithm and filter the messages to a junk SMS folder. Scam SMSes will be sent to NCPC and SPF for collation. This keeps the app updated and will help protect others from such scam calls and messages.
Report scam messages – You can also report scam messages from other chat apps such as WhatsApp, Wechat, IMO, Viber, etc. You can forward the messages via ScamShield’s in-app reporting function.
ScamShield is an initiative by the Singapore Police Force and the National Crime Prevention Council, and more information can be found at https://www.scamshield.org.sg/.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals. DBS will never use voice or instant messaging apps like Whatsapp or Viber to contact you.
Contact us through our chatbot or call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Fraudulent Mobile Application Alert
Date: 24 December 2020
Description: Scammers are hosting fraudulent mobile applications on non-DBS websites, or approved application stores to defraud and scam our customers. The websites and mobile applications are masquerading as the DBS Digital Exchange to target existing and potential DBS and POSB customers. Customers who click on the link will be asked to install a fraudulent DBS mobile application that claims to allow for digital currency transactions.
Should customers fall victim and install the malicious applications, they may be asked to transfer funds to the fraudulent applications to purchase cryptocurrency. If provided, the scammers would siphon off the transferred funds without delivery of the purchased cryptocurrency.
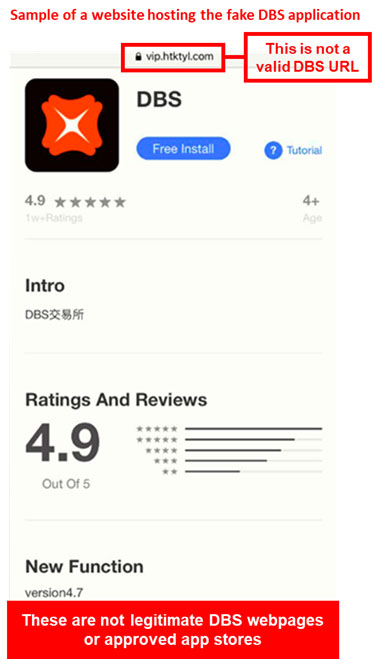
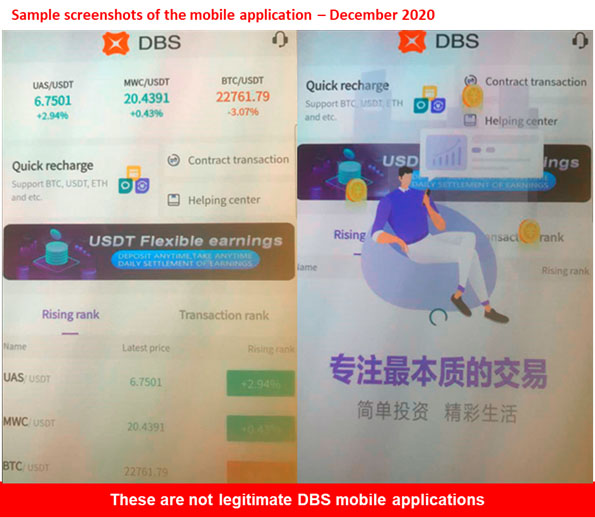
Who might be at risk?
DBS and POSB iBanking customers
How can you protect yourself from this?
- Be alert and always verify the details in messages from DBS and POSB. Always check that the message reflects your intended actions and do not proceed or authorize suspicious transactions.
- Always type in the URL of DBS website directly into the address bar of your browser. If you are on mobile, consider using our official DBS or POSB Digibank applications.
- Only download and install mobile applications from legitimate sources. Always download and install mobile apps from authoritative sources such as Google Play Store or Apple App Store to ensure that the application is legitimate.
- Never reply to unsolicited SMSs or emails. Responses to such SMSs or emails could be used by fraudsters to socially engineer information or trick users into performing unwanted actions. Be cautious of “unsubscribe” links as these may also be used to socially engineer information as well.
- DBS will never request for your PIN, password or OTP through phone call, email or SMS. Call us immediately at 1800 111 1111 (Personal Banking) or 1800 222 2200 (Business Banking), if you notice unknown transactions appearing on your account. Customers are also encouraged to use the latest versions of internet browsers available, which may provide advanced security features such as anti-phishing and forged website identification. If such features are available, customers are advised to turn them on.
Customer Advisory Voice Phishing
Date: 10 December 2020
Who might be at risk?
DBS and POSB customers
Description: Scammers are hosting fraudulent applications on Apple Test Flight program to defraud and scam our customers.
The Apple Test Flight program is a program offered by Apple for developers to host their applications under development for user testing. We have found scammers abusing this legitimate program by hosting fraudulent DBS applications on the platform to steal customers’ confidential information such as username, password and one-time pin.
These applications utilize our logo and branding to add a veneer of legitimacy to convince unsuspecting victims to install the fraudulent applications.
Should an individual fall victim and install such applications, these applications may attempt to siphon sensitive customer data, conduct fraudulent funds transfers, or request the victim conduct the following actions:
- Provide Internet Banking credentials including SMS and email one-time pin,
- Add payee or transfer fund to another account,
- Approve the provision of DBS’ Digital Token on a device not owned by the victim.
Customers are advised to be mindful of any applications they install.
- DBS will not request for users to be a part of an Apple Test Flight program. Only use our official applications that may be downloaded via Apple Store, Google Play Store, or other DBS-official applications.
- Remember: Do not give out your Internet Banking credentials, OTP, or Digital Token approval to unknown individuals, applications, or websites.
- Call us immediately at the hotlines below if you receive such a call or suspect you’re a victim of fraud. If available, you may choose to use our chatbot to report this fraud as well.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Social Media Phishing Alert
Date: 20 October 2020 (first posted on 12 October 2020)
Who might be at risk?
DBS and POSB customers
Description: Scammers are actively targeting DBS customers through advertisements on social media platforms. These advertisements masquerade as a DBS giveaway to entice unsuspecting customers to click on the malicious links to phishing sites.
Should a customer fall victim and click on the link, the page may ask for the customer to provide their:
- Internet Banking credentials,
- OTP or Digital Token approval,
- Performing fund transfer(s) to another account.

Customers are advised to be mindful of such advertisements on social media and go directly to our website or DBS-owned social media pages.
If you notice a similar advertisement or are contacted through social media by individuals claiming to be associated with DBS, stop, check, and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Stay updated on the latest security news that might affect the way you bank online.
Phishing Alert
Date: 04 November 2020
Who might be at risk?
DBS and POSB customers
Description: Scammers are actively targeting DBS customers through phishing SMS and websites. These SMSes masquerade as an ATM Card alert and provide a link.
Customers visiting these sites are directed to a login page mimicking DBS’s Internet Banking website. These websites ask for their Internet Banking username-password combination as well as a customer’s phone number.
If a customer falls victim to this scam, the scammer will call the customer and may ask for sensitive information such as Digital Token approval or verification codes sent to the customer’s email or phone number. The provided information may be used to conduct unwanted fund transfers or install the customer’s Digital Token on the scammer's phone.
The affected customer’s Digital Token will be disabled on their phone, allowing for the scammer to conduct unwanted fund transfers and modifications while preventing the customer from accessing banking features.
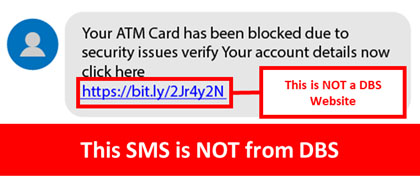

Customers are advised to be mindful of such SMS and to go directly to our website instead of clicking links in such SMS.
If you receive a similar email or have been contacted by individuals claiming to be DBS staff, stop, check and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals. DBS will never use voice or instant messaging apps like Whatsapp or Viber to contact you.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Social Media Phishing Alert
Date: 20 October 2020 (first posted on 12 October 2020)
Who might be at risk?
DBS and POSB customers
Description: Scammers are actively targeting DBS customers through advertisements on social media platforms. These advertisements masquerade as a DBS giveaway to entice unsuspecting customers to click on the malicious links to phishing sites.
Should a customer fall victim and click on the link, the page may ask for the customer to provide their:
- Internet Banking credentials,
- OTP or Digital Token approval,
- Performing fund transfer(s) to another account.

Customers are advised to be mindful of such advertisements on social media and go directly to our website or dbs-owned social media pages.
If you notice a similar advertisement or are contacted through social media by individuals claiming to be associated with DBS, stop, check, and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 24 September 2020
Who might be at risk?
DBS and POSB customers
Description: We have detected phishing websites attempting to take control of DBS and POSB customers’ DBS Digital Token and allowing a scammer to install the Digital Token on their phone in order to conduct fraudulent transactions.
Customers visiting these sites are directed to a login page mimicking DBS’s Internet Banking website. These websites ask for their Internet Banking username-password combination as well as verification codes sent to their email and mobile phone via SMS.
If a customer falls victim to this scam, their DBS Digital Token will be installed on the scammer's phone, giving the scammer full access to the customer’s bank account in order to conduct unwanted transactions. The affected customer’s Digital Token will be disabled on their phone, preventing the customer from conducting fund transfers or modifications to their account.
If you receive a similar email or have been contacted by individuals claiming to be DBS staff, stop, check and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, Digital Token, or any DBS-related email or SMS verification approvals to other individuals.
If you are having issues using your DBS Digital Token or suspect you have provided your DBS credentials, OTPs, Digital Token approvals, or any DBS-related email or SMS verification codes to unauthorized parties, call our official hotline numbers immediately for assistance.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Email and Voice Phishing Advisory
Date: 21 September 2020
Who might be at risk?
DBS and POSB customers
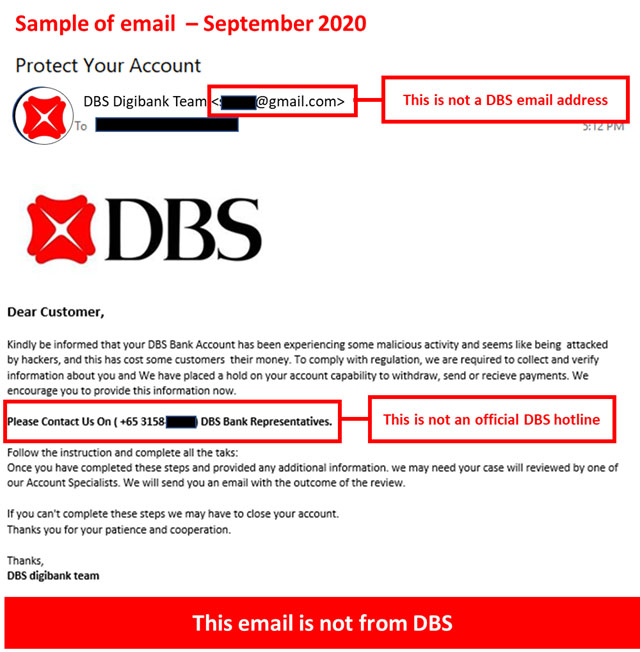
Description: Scammers are targeting customers through fraudulent account advisory emails asking customers to call a non-DBS number.
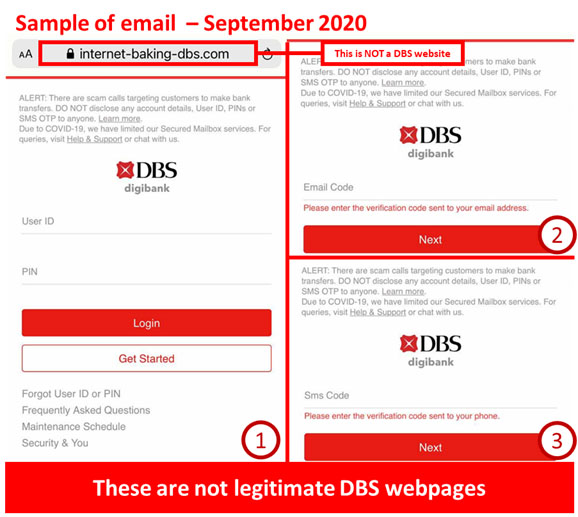
If a customer calls this number, the scammer impersonates a DBS staff and may ask for any of the following:
• Internet Banking credentials,
• OTP or Digital Token approval,
• Performing fund transfer(s) to another account.
Should a customer provide this information, the scammers may conduct unauthorized card or account transactions.
Customers are advised to be mindful of such emails and go directly to our website to access our official hotline numbers.
If you receive a similar email or have been contacted by individuals claiming to be DBS staff, stop, check and exercise caution before you act.
Remember: Do not give out your Internet Banking credentials, OTP, or Digital Token approval to other individuals. If you suspect you have provided your DBS credentials, OTPs, or Digital Token approval to unauthorized parties, call the official hotlines immediately in order to verify if these calls are legitimate.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 10 August 2020
Who might be at risk?
DBS and POSB customers
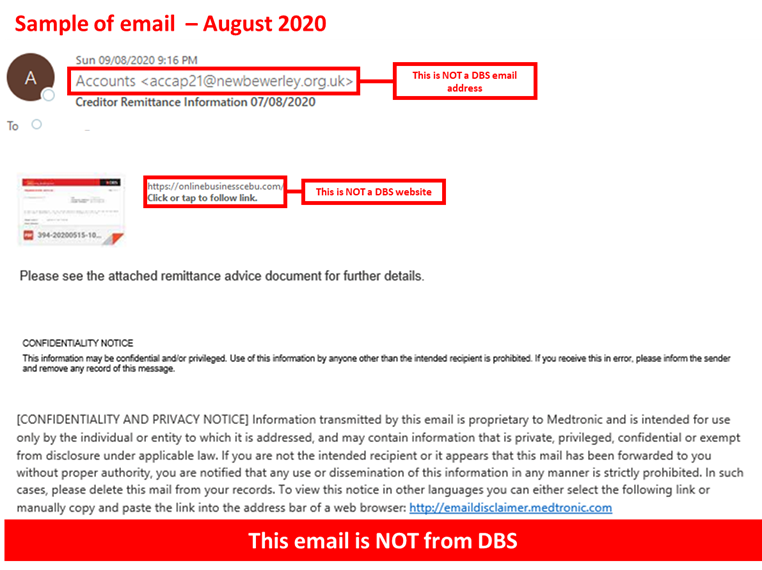
Description: We have detected phishing emails and web pages targeting DBS and POSB customers. These phishing emails are sent from a non-DBS email, with an attachment masquerading as a creditor remittance advice from DBS. If a customer falls victim and clicks on the attachment, they will be redirected to a website to download and install a malicious software or malware. Once installed, the malware would allow the scammers to access the customers’ computers and steal sensitive information such as login credentials to the DBS Internet Banking website.
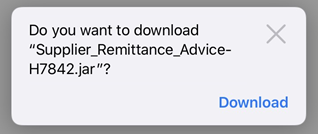
Customers are advised to be mindful of such emails.
- If you receive a similar email, stop, check and exercise caution before you act.
- Never reply to unsolicited SMSs or emails. Responses to such SMSs or emails could be used by fraudsters to socially engineer information or trick users into performing unwanted actions. Be cautious of “unsubscribe” links, as these may also be used to socially engineer information as well.
- Be alert and always verify the details in messages from DBS and POSB. Always check that the message reflects your intended actions and do not proceed or authorize suspicious transactions.
- Always type in the URL of DBS website directly into the address bar of your browser. If you are on mobile, consider using our official DBS or POSB Digibank applications.
- Customers are also encouraged to use the latest versions of internet browsers available, which may provide advanced security features such as anti-phishing and forged website identification. If such features are available, customers are advised to turn them on.
- DBS will never request for customers to install software to access our banking websites, or ask for your PIN, password or OTP through phone call, email or SMS.Do not give out your Internet Banking credentials, OTP, or Digital Token approval to other individuals.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Voice Phishing Advisory
Date: 11 June 2020
Who might be at risk?
DBS and POSB customers
Description: Scammers are targeting customers through voice calls and claiming there are issues with their DBS account. If a customer picks up a call, an automated voice message plays and claims there are issues with a customer’s account and requests for the customer to press a number to reach a live caller.
If a customer proceeds further, the scammer impersonates a DBS staff and may ask for any of the following:
• Internet Banking credentials,
• OTP or Digital Token approval,
• Performing fund transfer(s) to another account.
Should a customer provide this information, the scammers may conduct unauthorized card transactions.
Customers are advised to be mindful of such calls.
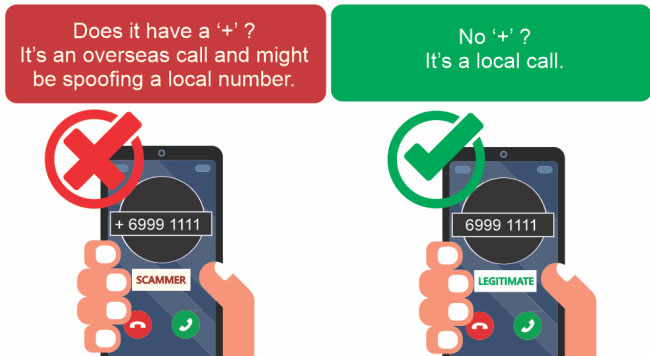
- Customers in Singapore are advised that all international calls have a ‘+’ prefix. DBS will never call you from a number with a ‘+’ prefix when you are in Singapore.
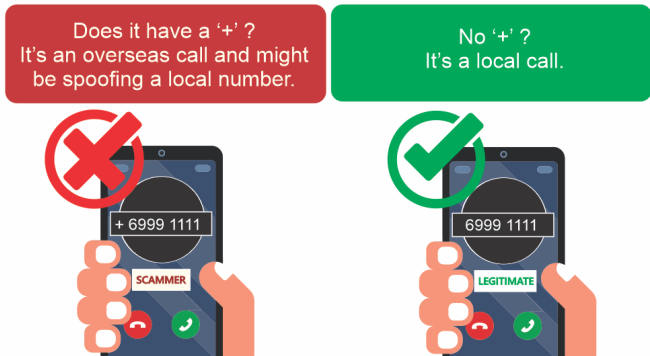
- If you receive a similar call or have been contacted by individuals claiming to be DBS staff, stop, check and exercise caution before you act.
- Remember: Do not give out your Internet Banking credentials, OTP, or Digital Token approval to other individuals. If you suspect you have provided your DBS credentials, OTPs, or Digital Token approval to unauthorized parties, call the official hotlines immediately in order to verify if these calls are legitimate.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Phishing Alert
Date: 02 March 2020
Who might be at risk?
DBS and POSB customers
Description: We have detected a number of phishing emails claiming to be DBS or POSB credit or debit card activation emails. These emails request for the recipient to click on a link to a malicious website and are directed to provide their card details, personal information, and a secondary OTP.
Should a customer provide this information, the scammers may conduct unauthorized card transactions.
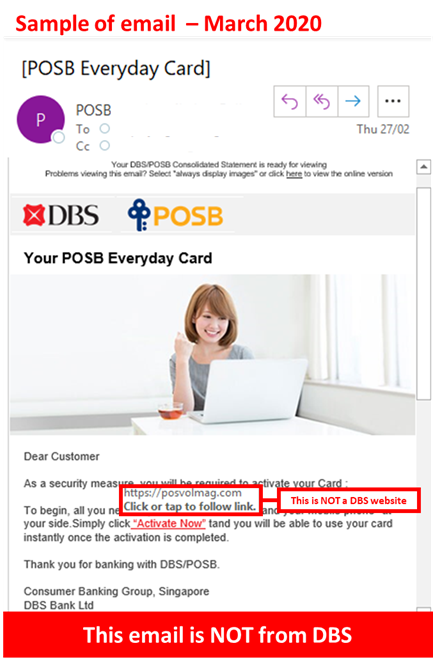
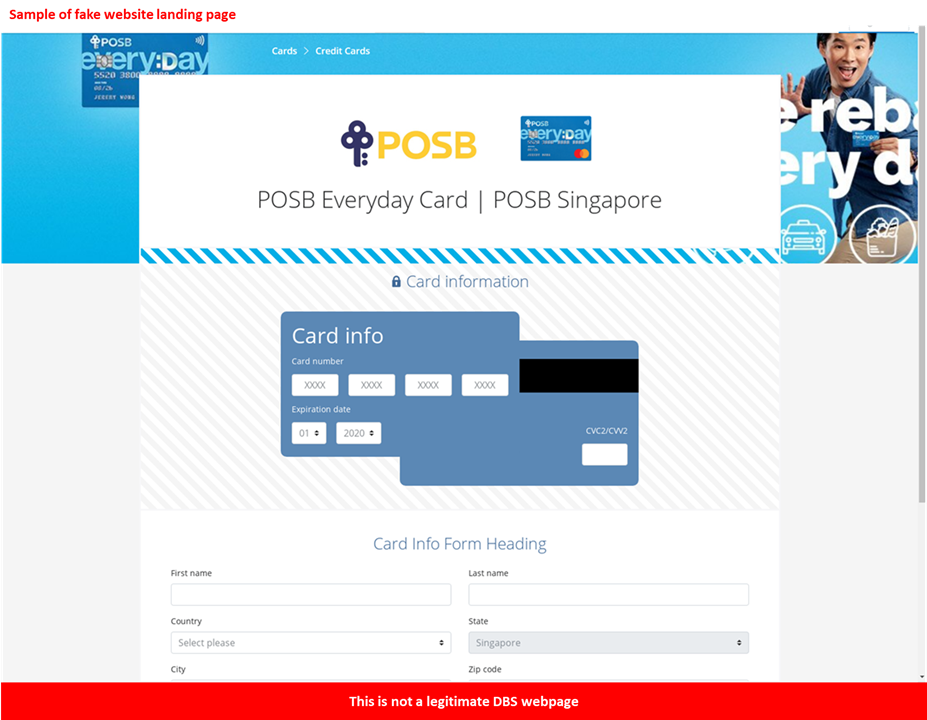
Customers are advised to be mindful of such calls.
- DBS will not request for customers to activate their credit or debit cards through a non-DBS website. For more information on card activation, please visit https://www.dbs.com.sg/personal/support/card-activate-new-card.html
- Verify the details in messages from DBS and POSB. Always check that the message comes from DBS and reflects your intended actions. Do not proceed further or authorize suspicious transactions. Go directly to DBS or POSB’s website or use our mobile applications in order to access our services.
- Remember: Do not give out your credit or debit card details, OTP, or Digital Token approval to unverified individuals. If you suspect you have provided your DBS credit or debit card details, OTPs, or Digital Token approval to unauthorized parties, call us immediately in order to verify if these calls are legitimate.
Call us immediately at the hotlines below if you suspect you’re a victim of fraud or notice any unexpected banking or card transactions.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Customer Advisory Voice Phishing
Date: 25 February 2020
Who might be at risk?
DBS and POSB customers
Description: Scammers are targeting customers through voice calls and claiming to assist with enrolment in DBS’s Complimentary COVID-19 Hospital Cash Insurance. If an individual falls victim to these claims, the scammer may ask for the following information or request the victim conduct the following actions:
- Internet Banking credentials,
- OTP or Digital Token approval,
- Performing fund transfer(s) to another account,
- Enable DBS’s Digital Token approval on a device not owned by the victim.
Customers are advised to be mindful of such calls.
- DBS will not call customers to enrol in the COVID-19 Hospital Cash Insurance program. Sign-ups are only available at our branches or through DBS’s website. Do not proceed further if you suspect a caller is asking you to reveal sensitive personal information (such as account information or credentials) or conduct suspicious or unfamiliar actions or transactions. For more information on the insurance program, please visit https://www.dbs.com.sg/personal/insurance/protection/protection-plans/covid-19-hospital-cash
- Remember: Do not give out your Internet Banking credentials, OTP, or Digital Token approval to other individuals. If you suspect you have provided your DBS credentials, OTPs, or Digital Token approval to unauthorized parties, call the official hotlines immediately in order to verify if these calls are legitimate.
- Learn more about Impersonation Scams at https://scamalert.sg/scam-details/impersonation-scam
Call us immediately at the hotlines below if you receive such a call or suspect you’re a victim of fraud.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Customer Advisory Voice Phishing
Date: 11 February 2020
Who might be at risk?
DBS and POSB customers
Description: The Singapore Police Force (SPF) has alerted the public regarding scams using the Novel Coronavirus (2019-nCoV) outbreak as bait. These scammers purport to be from the Singaporean Ministry of Health (MOH) and claim to conduct contract tracing to detect potentially infected individuals. If an individual falls victim to these claims, the scammer may ask for the following information or request the victim conduct the following actions:
- Internet Banking credentials,
- OTP or Digital Token approval,
- Performing fund transfer(s) to another account.
Similar scams in the past have impersonated SPF, Singtel, or DBS Staff.
Customers are advised to be mindful of such calls.
- MOH will never ask for your financial details during contact tracing calls. Verify these calls with the MOH hotline (6325-9220) if you receive such calls. Do not proceed further if you suspect a caller is asking you to conduct suspicious or unfamiliar actions or transactions.
- Remember: Do not give out your Internet Banking credentials, OTP, or Digital Token approval to other individuals. If you suspect you have provided your DBS credentials, OTPs, or Digital Token approval to unauthorized parties, call the official hotlines in order to verify if these calls are legitimate.
References:
The Straits Times, last retrieved on 11 Feb 2020, 1430hrs GMT+8
Call us immediately at the hotlines below if you receive or suspect you’re a victim of fraud.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
Customer Advisory Voice Phishing
Date: 06 February 2020
Who might be at risk?
DBS and POSB customers
Description: Scammers are actively targeting DBS customers through voice calls across various messaging platforms. A recent wave of such calls utilize Viber’s messaging platform and purports to be an official DBS hotline number in order to steal sensitive or financial information. The scammer impersonates DBS staff and claims a customer’s account is experiencing issues or being hacked and may attempt to trick the customer into performing the following actions:
- Provide internet banking credentials and/or OTP or Digital Token approval
- Provide credit card numbers and CVV
- Perform fund transfer(s) to another account.
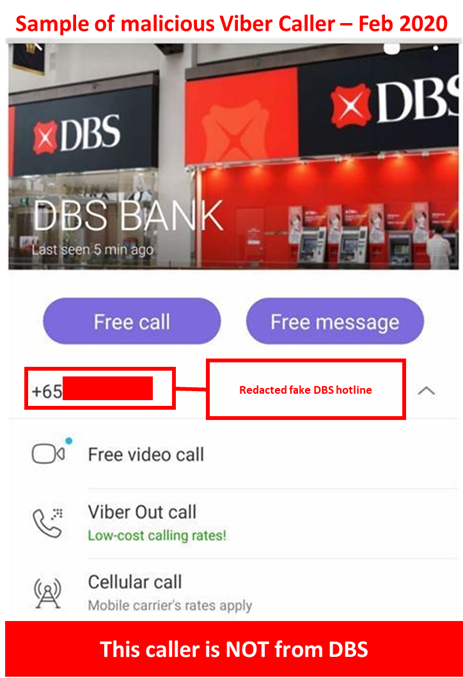
Customers are advised to be mindful of such calls.
- From 15 April 2020, all international calls will have “+” prefix. DBS will never call you from a number with a ‘+’ prefix when you are in Singapore.
- DBS will never call via Viber or any other voice or instant messaging application.
- Remember: DBS will never ask for you to provide your Internet Banking credentials, OTP, or Digital Token approval.
- If you receive a similar call, message, or have been contacted by individuals claiming to be DBS staff using any of the above methods, stop, check and exercise caution before you answer a call.
Call us immediately at the hotlines below if you receive or suspect you’re a victim of fraud.
Singapore: 1800-339-6963 or 6339-6963
China: 400-820-8988
Hong Kong: 2290 8888
India: 1-860-210-3456
Indonesia: 0804 1500 327
Taiwan: (02) 6612 9889 / 0800 808 889
